Mac utilizes Keychain Access for managing installed digital certificates. In addition, Keychain Access manages digital certificates and the following information.
- Accounts (ID and Password)
- Secret Memos
- Degital certificates
- Public keys
- Private keys
This article describes how to export a digital certificate.
About export from the Xcode
Use Xcode to export certificates presented by the Apple Developer Program for use in iOS app development and other applications in bulk. For more information, please see the following article.

This article describes how to specify individual certificates for export instead of batch export.
How to export keys with private keys
To export the private and the public keys, proceed as follows.
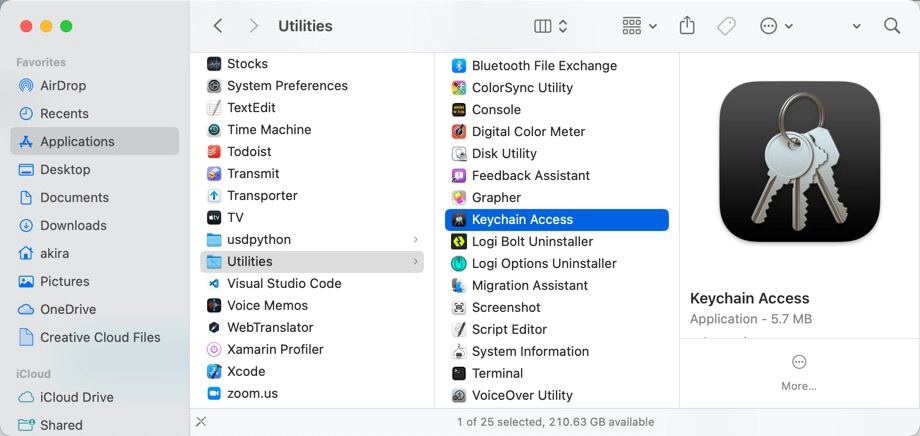
Select “System” or “System Roots” for certificates initially installed on the system.
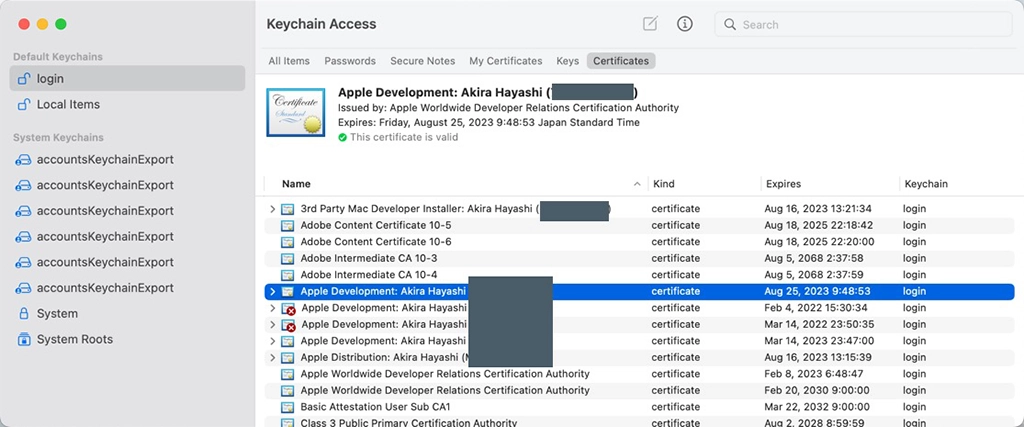
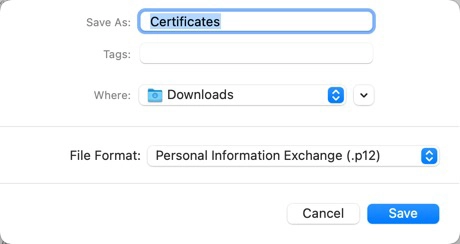
書き出されるファイルは入力したパスワードで暗号化されます。
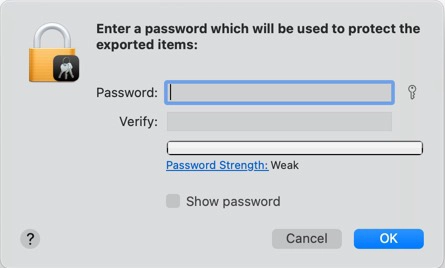
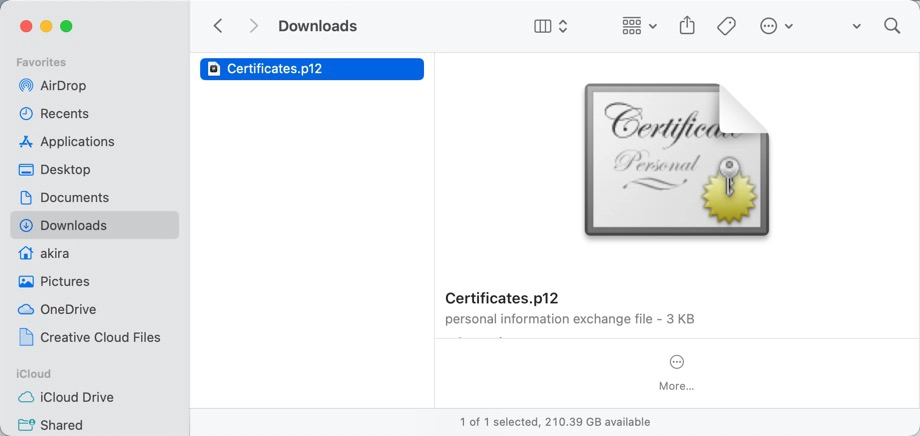
Verify if the key is included
Verify that the exported certificate contains the key. Since we have exported a certificate with a private key, we need to confirm that the exported certificate includes the private key. The certificate information is checked using openssl.
Run the following command in the Terminal.
% openssl pkcs12 -in certificate -noout -infoFor example, when the certificate file is Certificates.p12, do as follows.
% openssl pkcs12 -in Certificates.p12 -noout -info
Enter Import Password:
MAC Iteration 1
MAC verified OK
PKCS7 Encrypted data: pbeWithSHA1And40BitRC2-CBC, Iteration 2048
Certificate bag
PKCS7 Data
Shrouded Keybag: pbeWithSHA1And3-KeyTripleDES-CBC, Iteration 2048You will find that the following two pieces of information are contained in the certificate.
Certificate bag(Certificate)Shrounded Keybag(Key)
We have confirmed that both the certificate and the key are outp
How to export an X.509 certificate
Keychain Access can also export X.509 certificates. To export an X.509 certificate, select “Certificate (.cer)” from “File Format” in the Export dialog.
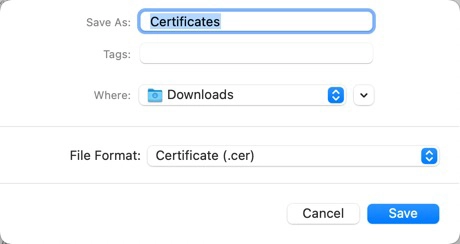
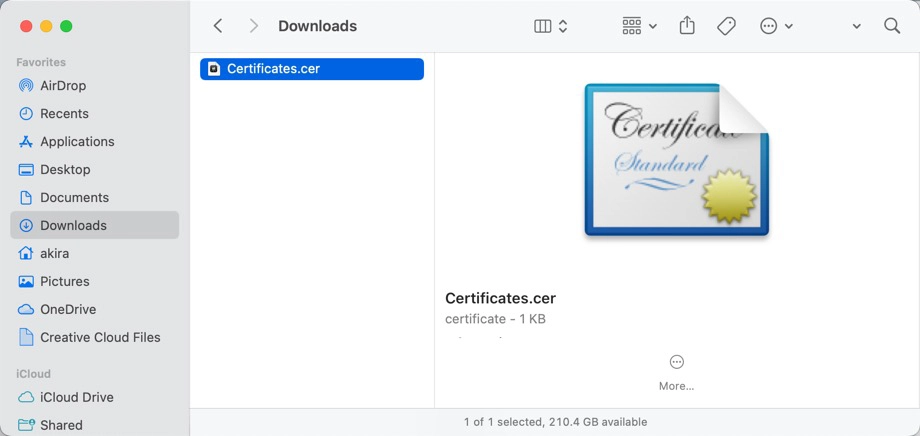
Check the contents of the exported X.509 certificate
Check that the exported X.509 certificate contains the selected certificate and public key. Use `openssl` to check.
% openssl x509 -inform der -noout -subject -in Certificates.cerThe output is then as follows.
subject= /UID=XXXXXXXXXX/CN=Apple Development: Akira Hayashi (0123456789)/OU=0123456789/O=Akira Hayashi/C=USThe name displayed in the keychain access matches the name written in the CN, so the selected certificate is exported. Also, when the following is executed, the public key in the certificate is output, and it can be confirmed that the public key is in the certificate.
% openssl x509 -inform der -noout -pubkey -in Certificates.cer
-----BEGIN PUBLIC KEY-----
(omit)
-----END PUBLIC KEY-----